Free Downloads: Cryptographic Algorithm
License: All | Free
The MD5 Message-Digest Algorithm is a widely used Cryptographic hash function with a 128 -bit (16-byte) hash value.
MDFiveCheck is a simple .NET ClickOnce MD5 checker application that can either validate or create an MD5 Checksum for any given file.
Category: Software Development / Misc. Programming
Publisher: Andy Gumbrecht, License: Freeware, Price: USD $0.00, File Size: 416.5 KB
Platform: Windows
SumChecker is simple utility to calculate and check MD5, SHA1, SHA256 and SHA512 file hashes.
SumChecker is simple utility to calculate and check MD5, SHA1, SHA256 and SHA512 file hashes. The MD5 Message-Digest Algorithm is a widely used Cryptographic hash function with a 128-bit (16-byte) hash value. In cryptography, SHA-1 is a Cryptographic hash function designed by the National Security Agency and published by the NIST as a U.S. Federal Information Processing...
Category: Utilities / Misc. Utilities
Publisher: Strizhevsky Artem, License: Freeware, Price: USD $0.00, File Size: 779.0 KB
Platform: Windows
Cryptographic Text Converter provides a Notepad with built-in encryption.
Cryptographic Text Converter provides a Notepad with built-in encryption. The encryption uses 128-bit AES (Advanced Encryption Standard). You can be confident that nobody will be able to break the encryption other than by guessing your user ID and passwor
Category: Utilities / Misc. Utilities
Publisher: sourceforge.net, License: Freeware, Price: USD $0.00, File Size: 816.0 KB
Platform: Windows, Mac, Vista
EFT Calculator is an application that performs common Cryptographic operations used in electronic funds transfer applications.
Main features:
- Cryptographic DES/3DES operations.
- Calculate a clear and encrypted PIN block and find the PIN from an encrypted PIN block.
- Calculate a CVV.
- Calculate a Visa PVV.
- Calculate and...
Category: Business & Finance / Calculators
Publisher: NTG, License: Freeware, Price: USD $0.00, File Size: 469.1 KB
Platform: Windows
Cryptographic text editor based on OrdoEmacs.
Cryptographic text editor based on OrdoEmacs. Uses anti-key logging techniques for additional paranoia. Includes Delphi source. Freeware with nice simple interface. Encrypt to file or to/from clipboard.
Category: Security & Privacy / Encrypting
Publisher: Wuul, License: Freeware, Price: USD $0.00, File Size: 488.0 KB
Platform: Windows
VSCryptoHash is a cryptographic hash calculation software.
VSCryptoHash is a Cryptographic hash calculation software. Simply drag and drop files (or type the text) in this calculator and hash string for the files (or for entered text) will be immediately displayed. Great tool for network administrators and webmas
Category: Utilities / Security & Encryption
Publisher: lokibit.com, License: Freeware, Price: USD $0.00, File Size: 1.4 MB
Platform: Windows, Vista, 7 (32-Bit, 64-Bit)




 Freeware
FreewareDatum Locker assists safe record keeping of account credentials and note taking which are deemed sensitive. Its strength comes from the use of Nullox's linearistic distance Cryptographic (LDC) Algorithm to securely store your data on disk thereby presenting an intruder with random symbols due to the omittance of a valid key. Datum Locker operates on a timer thus monitoring when...
Category: Security & Privacy / Anti-Spam & Anti-Spy Tools
Publisher: Nullox Software, License: Freeware, Price: USD $0.00, File Size: 522.0 KB
Platform: Windows
Encrypt and decrypt files, documents, and archives through major cryptographic standards
Encrypt and decrypt files, documents, and archives through major Cryptographic standards, including, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice. Features: *Strong encryption : Support for Cryptographic standards, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice....
Category: Security & Privacy / Encrypting
Publisher: 3nity Softwares, License: Freeware, Price: USD $0.00, File Size: 1.6 MB
Platform: Windows
Omziff is a straightforward encryption utility that uses various Cryptographic algorithms to encrypt and decrypt textual files. These algorithms include: Blowfish, Cast128, Gost, IDEA, Misty1, AES/Rijndael, and Twofish. Omziff will also generate random passwords, splits files and does simple file shredding according to DOD Standards. It is freeware, comes in a standalone executable file...
Category: Security & Privacy / Encrypting
Publisher: xtort.net, License: Freeware, Price: USD $0.00, File Size: 407.0 KB
Platform: Windows, All
With Febooti fileTweak Hash & CRC it is possible to compute most popular file hash checksums (such as MD5, CRC32, SHA-1 and other) in order to verify file integrity (if Cryptographic hash value is provided) or to supplement file with checksum, thus creating a possibility to verify the file upon further need.
Full list of supported Cryptographic hash checksum...
Category: Desktop Enhancements / Shell & Desktop Managers
Publisher: febooti software, License: Freeware, Price: USD $0.00, File Size: 788.3 KB
Platform: Windows
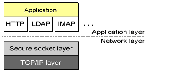
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are Cryptographic protocols that provide communications security over the Internet. TLS and SSL encrypt the segments of network connections above the Transport Layer.
Category: Security & Privacy / Encrypting
Publisher: SSL Protocol, License: Freeware, Price: USD $0.00, File Size: 106.0 KB
Platform: Windows, Linux, Mac
ALVIS Live! is a new breed of Algorithm visualization technology that supports the rapid construction and interactive presentation of "low fidelity" Algorithm visualizations. The two primary goals of ALVIS are to empower novice programmers to construct algorithms and accompanying visualizations that involve array iteration; and to to facilitate educationally-beneficial...
Category: Software Development / Help File Utilities
Publisher: VEUPL, License: Freeware, Price: USD $0.00, File Size: 6.5 MB
Platform: Windows
The regular grid algorithm advances between cells similar to Bresenham's line algorithm.
The regular grid Algorithm advances between cells similar to Bresenham's line Algorithm. It considers the evenly-spaced, infinite planes that separates cells. You can think of a ray like a particle traveling at constant rate away from the observer. The components of the particle’s velocity vector are independent of each other. Meaning, the time required for the particle...
Category: Multimedia & Design / Multimedia App's
Publisher: meatfighter.com, License: Freeware, Price: USD $0.00, File Size: 8.8 KB
Platform: Windows
VT Hash Check adds a Windows Explorer context menu item to compute the MD5 hash checksum of any file and to then send that checksum for checking against their Virus database.
By default, only the MD5 hash is computed. The MD5 hash Algorithm is vulnerable to theoretical collisions and has been recommended to be avoided for Cryptographic functions requiring a high level of...
Category: Security & Privacy / Other
Publisher: Boredom Software, License: Freeware, Price: USD $0.00, File Size: 1.9 MB
Platform: Windows
Polar Crypto Light is simple to use, supports the securest, most recommended Cryptographic standards and crypto systems. It is an ActiveX control which seamlessly adds encryption features to your Windows applications. It is easy to use, it encrypts strings, buffers and files. It uses public and private RSA keys for encryption/decryption (256-bit symmetric keys for AES) and provides...
Category: Software Development / Components & Libraries
Publisher: Polar, License: Freeware, Price: USD $0.00, File Size: 6.1 MB
Platform: Windows
This multi-user system and its companion (Crypto Distributor) are parts of a crypto-system based on established asymmetric public key and symmetric key crypto-algorithms (such as RSA and AES). It is the first embodiment of our next generation soft token based declarative Cryptographic key, access right and digital source distribution and management technology. It can be used as a...
Category: Security & Privacy / Encrypting
Publisher: CryptoGateway Software Inc, License: Freeware, Price: USD $0.00, File Size: 3.7 MB
Platform: Windows
This application was designed to help you create random passwords, using the fgrand (pseudo-random generator good enough for Cryptographic purposes). With this program, you can save any password that you create and password that you save can be displayed in the FG Password Generator.
Category: Security & Privacy / Password Managers & Generators
Publisher: FreeStone Group, License: Freeware, Price: USD $0.00, File Size: 177.0 KB
Platform: Windows
FileEncrypter is a small freeware utility that is capable of encrypting any file on any media storage with the officially recognized encryption Algorithm - AES (Rijndael). The key length of the Algorithm may vary from 128 to 256 bit to ensure the maximum protection of encrypted information.The use of FileEncryptor will help you to keep all important files safe no matter what...
Category: Utilities / System Utilities
Publisher: ARXsoft Co., Ltd., License: Freeware, Price: USD $0.00, File Size: 388.0 KB
Platform: Windows
MSTMD5 is a program that tells you the md5 result of a file.
MSTMD5 is a program that tells you the md5 result of a file. The MD5 is a Cryptographic implementation Algorithm represented typically with a 32 hexadecimal digit. This system is widely used and accepted as a security implementation. It’s used to verify the integrity or the authenticity of a file. With this program you can check for example, a file downloaded from the...
Category: Utilities / Misc. Utilities
Publisher: mst software GmbH, License: Freeware, Price: USD $0.00, File Size: 923.9 KB
Platform: Windows
LFX-1310 is a Free plug-in multi-effector including 24 types of algorithm and 3 serial slots.
LFX-1310 is a Free plug-in multi-effector including 24 types of Algorithm and 3 serial slots. This freeware is the stand-alone version of Effecting Module of Ravity(S) & Ravity(R). Every Algorithm realizes the very effect you have on your mind, and is fully optimized for low CPU load.
Category: Audio / Music Creation
Publisher: LUXONIX, License: Freeware, Price: USD $0.00, File Size: 1.1 MB
Platform: Windows
GASolver is an automated genetic Algorithm driven solver for Excel spreadsheet based solution seeking. Using a genetic Algorithm avoids many of the problems found with linear solvers when solving for example large problems with multiple variables. GASolver has been developed over the last 10 years to help you evolve better solutions.
Category: Home & Education / Mathematics
Publisher: Yearstretch Limited, License: Freeware, Price: USD $0.00, File Size: 2.8 MB
Platform: Windows
KJLZip.DLL provides functions to compress a file using a proprietary compression Algorithm, and decompress files compressed by the proprietary Algorithm.
Category: Software Development / Misc. Programming
Publisher: kjlsoftware.com, License: Freeware, Price: USD $0.00, File Size: 33.0 KB
Platform: Windows, Mac, 2K
BeeGui uses as compression Algorithm the core of Bee, a sophisticated Algorithm created by Andrew Filinsky; the technique used for the data compression is based on the use of a PPM modeller (Prediction with Partial string Matching) and of a kind of Range Coder as codifier. Result is high level of compression and good speed.
Category: Utilities / File Compression
Publisher: Andrew Filinsky and Melchiorre Caruso, License: Freeware, Price: USD $0.00, File Size: 664.2 KB
Platform: Windows
EaseFilter File System Encryption Filter Driver SDK provides you a comprehensive security solution to develop transparent file level encryption products, it allows you to encrypt the files on-the-fly, it can allow only authorized users or processes to access the encrypted files. Supported strong Cryptographic Algorithm Rijndael is a high security Algorithm which was chosen...
Category: Security & Privacy / Encrypting
Publisher: EaseFilter Inc., License: Freeware, Price: USD $0.00, File Size: 4.0 MB
Platform: Windows
XHash is a file hash value calculator, presently supports MD5, SHA-1, CRC32 algorithm; and supports Base64 common algorithm.
Category: Utilities / File & Disk Management
Publisher: gadgets-mike.appspot.com, License: Freeware, Price: USD $0.00, File Size: 33.6 KB
Platform: Windows, Vista
This software can compress data using LZ77 algorithm.
This software can compress data using LZ77 Algorithm. MsCompress is a Microsoft "compress.exe/expand.exe" compatible (de)compressor. This package contains two programs:
- msexpand, which decompresses files compressed by Microsoft compress.exe utility (e.g. Win 3.x installation files)
- mscompress, which compresses files using LZ77 compression Algorithm....
Category: Utilities / File Compression
Publisher: GnuWin32, License: Freeware, Price: USD $0.00, File Size: 318.6 KB
Platform: Windows
There are a lot of password generators available in the Internet.
There are a lot of password generators available in the Internet. Some of them use standard pseudorandom number generators which are unsuitable for Cryptographic purposes. Such generators create weak passwords and must never be used! LastBit Password Generator is a Cryptographic random generator, so all generated passwords are of good quality. LastBit Password Generator is...
Category: Security & Privacy / Other
Publisher: LastBit Software, License: Freeware, Price: USD $0.00, File Size: 54.0 KB
Platform: Windows
AWR is an abbreviation for Action Wait Reverse.
AWR is an abbreviation for Action Wait Reverse. The AWR control Algorithm is one of the so-called ConX algorithms. Another example of a ConX Algorithm is a conventional PID controller. The AWR controller is an alternative to a PID controller. The AWR control Algorithm has been developed especially for control of processes with long time delays and large time constants,...
Category: Software Development / Misc. Programming
Publisher: Fuyang Automation, License: Freeware, Price: USD $0.00, File Size: 5.9 MB
Platform: Windows
BOSmakeable is uses the Deepfinesse algorithm to calculate makeable contracts.
BOSmakeable is uses the Deepfinesse Algorithm to calculate makeable contracts. It takes a dealfile in dlm-format as input.
BOS also makes links on desktop etc. unnecessary. By using BOS you can put all your programs on a USB-memory stick and can use them in the same way on any computer. If needed you must run the Memorystick program to get compatible system.
Category: Utilities / File Compression
Publisher: SackAb, License: Freeware, Price: USD $0.00, File Size: 85.0 KB
Platform: Windows
JHAVÉ is a java application that renders algorithm visualizations.
JHAVÉ is a java application that renders Algorithm visualizations. Students explore algorithms by viewing visual representations of data, controlling movement and by responding to pop-up questions. We provide a large collection of free materials for students and faculty to use.
Category: Multimedia & Design / Multimedia App's
Publisher: JHAVE, License: Freeware, Price: USD $0.00, File Size: 14.3 MB
Platform: Windows
File Encryptor is a small, but yet poweful and easy to use file encryption utility. File Encryptor allows you to encrypt your important files with an industrial-strength encryption Algorithm and send your confidential files to others over the Internet without worrying about the contents being read by anybody other than the recipient. Rijndael encryption Algorithm ensures...
Category: Utilities
Publisher: WhizApps, License: Freeware, Price: USD $0.00, File Size: 134.1 KB
Platform: Windows
In 1998 Neurotechnology developed VeriFinger, a fingerprint identification Algorithm, designed for biometric system integrators. Since that time, the company has released 14 Algorithm versions, with the current version, VeriFinger 6.3, providing the most powerful fingerprint recognition algorithms to date. VeriFinger 6.3 fingerprint engine performance and reliability has been...
Category: Security & Privacy / Access Control
Publisher: Neurotechnology, License: Freeware, Price: USD $0.00, File Size: 139.8 MB
Platform: Windows
File verification utility, uses SHA-2 algorithm. .
File verification utility, uses SHA-2 algorithm.
Category: Utilities
Publisher: eCat, License: Freeware, Price: USD $0.00, File Size: 221.1 KB
Platform: Windows
DLOCK2 is a simple command line file encryption/decryption utility program that uses the free Diamond 2 Encryption Algorithm. Full source code and documentation of the Algorithm and the master's thesis it is based on are included. It compiles with Gnu C++ and other compilers, so it can be adapted to many operating systems. Version 2.01 is the same as the original DLOCK2, except...
Category: Utilities / Misc. Utilities
Publisher: Michael Paul Johnson, License: Freeware, Price: USD $0.00, File Size: 573.0 KB
Platform: Windows, Linux
Technical information:
Implemented in C# 4/.
Technical information:
Implemented in C# 4/.NET 4.
Platform used: Visual Studio 2010.
Graphics presentation using WPF 4.
Programming features:
Chess board implemented using the 0x88 representation.
Move searching using Alpha – Beta Pruning Algorithm (NegaScout Algorithm is also implemented).
Move ordering using the killer move...
Category: Games / Misc. Games
Publisher: Solidus, License: Freeware, Price: USD $0.00, File Size: 1.3 MB
Platform: Windows
The purpose of this program is to support users of data of the CHRIS sensor onboard of the ESA Proba platform. It provides extensions for BEAM, which allow accomplishing the following tasks: Noise reduction: Removes the vertical striping in CHRIS response-corrected images caused by the slit effect and a superposition of high-frequency noise. Cloud screening: Marks cloudy pixels in CHRIS...
Category: Business & Finance / Applications
Publisher: Brockmann Consult GmbH, License: Freeware, Price: USD $0.00, File Size: 114.0 MB
Platform: Windows
Improves quality of home/amateur video removing interlace effect and reducing noise
This product is created for the processing of the amateur video - for example, recorded on the home video equipment or inputted into the PC from TV-tuner or from TV-in of video card. It removes the interlace effect from video and reduces its noise level. The product incorporates the advanced technologies in the field of noise reduction and the unique Algorithm of the removing of the...
Category: Multimedia & Design / Video
Publisher: Alparysoft, License: Freeware, Price: USD $0.00, File Size: 314.0 KB
Platform: Unknown
The Algorithm used to build the code words that determine the receive and transmit frequencies in the PFX are interesting in themselves. However you do not need to know them if you have suitable software available that turns the desired TX/RX channel frequencies into codes and then puts them in sequence to build a file that can be blown into a PROM.
Category: Software Development / Misc. Programming
Publisher: Philips/Pye, License: Freeware, Price: USD $0.00, File Size: 59.1 KB
Platform: Windows
The SAR Training Processor (STP) is a graphical tool written to assist in learning and teaching the flow of SAR processing. After installation, you will have a start-menu shortcut that you can use to run the SAR Training Processor.A number of algorithms have been developed to effectively process SAR data from its raw signal into well focused images. The most common SAR processing...
Category: Multimedia & Design / Multimedia App's
Publisher: Alaska Satellite Facility Geophysical Institute, License: Freeware, Price: USD $0.00, File Size: 10.6 MB
Platform: Windows




 Freeware
FreewareWireless Network Viewer is a small utility that runs in the background, and monitor the activity of wireless networks around you. For each detected network, it displays the following information: SSID, Last Signal Quality, Average Signal Quality, Detection Counter, Authentication Algorithm, Cipher Algorithm, MAC Address, RSSI, Channel Frequency, Channel Number, and more.
Category: Internet / Monitoring
Publisher: 77Freeware, License: Freeware, Price: USD $0.00, File Size: 4.2 MB
Platform: Windows, Other
WirelessNetView is a small utility that runs in the background, and monitor the activity of wireless networks around you. For each detected network, it displays the following information: SSID, Last Signal Quality, Average Signal Quality, Detection Counter, Authentication Algorithm, Cipher Algorithm, and more.
Category: Internet / Monitoring
Publisher: NirSoft Freeware, License: Freeware, Price: USD $0.00, File Size: 36.0 KB
Platform: Windows
Data compression utility, which allows you to quickly open, create, and modify your archives. .
Data compression utility, which allows you to quickly open, create, and modify your archives.
Category: Audio
Publisher: Safe Soft Corporation, License: Freeware, Price: USD $0.00, File Size: 491.2 KB
Platform: Windows
This free file encryption software, uses a 192 bit Triple DES algorithm.
This free file encryption software, uses a 192 bit Triple DES Algorithm. Allows you to encrypt files and folders with just a click of the mouse. ABI- CODER is easy to use and comes with great help files as well as hints to guide you along the way. FREE- N
Category: Security & Privacy / Encrypting
Publisher: abisoft.net, License: Freeware, Price: USD $0.00, File Size: 1.2 MB
Platform: Windows, Mac, 2K
Free For EveryoneOne powerful file encryption for the Windows platform.
Free For EveryoneOne powerful file encryption for the Windows platform. Offers a bunch of new and improved features: 1. Four encryption algorithms (Blowfish, AES, MD5, Triple-DES). 2. Strong key support, handling and Cryptographic implementations. 3. Encrypts megabytes of file data per second on modern machines.
Category: Security & Privacy / Encrypting
Publisher: kakasoft, License: Freeware, Price: USD $0.00, File Size: 346.0 KB
Platform: Windows
KMB Text Compare implements a diff algorithm.
KMB Text Compare implements a diff Algorithm. The original idea for this program was to compare G-Code programs to check if there were any differences between versions and/or machines. This program is not limited to G-Code programs, but can compare any ty
Category: Business & Finance / Applications
Publisher: KMBPros.com, License: Freeware, Price: USD $0.00, File Size: 919.0 KB
Platform: Windows
100% assembly language written small (13,824 bytes) encryption utility that uses Blowfish encryption Algorithm in CBC mode. It is easy to use and support multiple files drag-and-drop. It is portable and run on your USB memory stick anywhere you go! Very u
Category: Security & Privacy / Encrypting
Publisher: picofactory.com, License: Freeware, Price: USD $0.00, File Size: 13.5 KB
Platform: Windows, 2K
Credit Card Checker Tool instantly check credit card number for validity.
Credit Card Checker Tool instantly check credit card number for validity. It verifies MasterCard, Visa, Carte Blanche, Diners Club, EnRoute, American Express (AMEX), Discover, JCB and other credit card numbers. Credit Card Check Tool utilizes LUHN10 Algorithm (except EnRoute) and first card digits verification Algorithm. * Verifies MasterCard, Visa, American Express, Discover,...
Category: Business & Finance / Calculators
Publisher: OnlineInvestingSite, License: Freeware, Price: USD $0.00, File Size: 272.0 KB
Platform: Windows, Unix
With a specially designed Algorithm, scans your hardware (CPU, RAM, Graphic Card, Hard Disk, CD/DVD, Modem ect.) and your software. Then applies the best values for over 50 powerful tweaks!
Category: Utilities / System Utilities
Publisher: Mz Ultimate Tools, License: Freeware, Price: USD $0.00, File Size: 885.0 KB
Platform: Windows
TopCoder Arena is a famous online competition for programmers to demonstrate their talent in Algorithm and programming. There are many talent people participated in it, and the competition time is not enough at all for most participators. You have to translate the problem description into the C++ class and method, design the Algorithm, implement, and test them manually. Now with...
Category: Software Development
Publisher: BossEye Inc., License: Freeware, Price: USD $0.00, File Size: 128.9 KB
Platform: Windows
File encryption/decryption tools with strongest AES algorithm.
File encryption/decryption tools with strongest AES Algorithm. Can generate the hash of the source file as password for symmetric encryption(64 digits password). Encryption strength AES Rijndael: 256 bit / Hash: SHA-256
Category: Security & Privacy / Encrypting
Publisher: communicrypt.com, License: Freeware, Price: USD $0.00, File Size: 1.4 MB
Platform: Windows